offline
- mpman

- Mod u pemziji
- Pridružio: 12 Okt 2010
- Poruke: 10910
|
Ovo je lepo objašnjeno:
Galaxitus ::This affect about 99% of the hardware in the world including the consoles, smartphone, tablet, PCs, etc.
To explain the Meltdown and Specter's effect, it's actually something quite simple to do:
You know the processor is basically the "task handler" of everything in your PC/Console/Tablet,etc. right? It runs those 0 & 1 at a super high speed.
The thing is that to run those 1 & 0, it has to, technically, store them in a physical way so that it can be passed through to what's next. As it's 0 & 1, it's not encrypted or protected. It's pure raw data. The encryption and protection are usually done after the data has passed through the processor... by a task handled by the processor (ironically). Now, what they have "found" (which is false. it's has been known since the 80's) is that it's possible to access this raw data by force feeding some 0 & 1 to the processor which can be hidden in anything and makes it start an hidden small software which, for example, could send a copy of the raw data through the web.
Since the 80's, it was said that it was relatively impossible to decrypt that raw data which pass through the processor as too much information is missing from their meaning. (Like if you're purchasing something through Paypal, the browser doesn't send the data (to be displayed) through the processor with a big "This is the key to this Paypal account". It's billions of 0 & 1 mixed together going in fast like actual lightning.
The most sensitive possible data that is easier to extract from this process are data like key-logs. Whenever you press any keys on your keyboards, the keyboard send a signal through the wire (or wireless signal) and the motherboard receive it one way or the other. It's a electrical and physical process that is easy to reverse engineer since it's identical regardless of the PC or console. Even consoles have this kind of feature in it, but it's just different. Same with tablet which has a digital keyboard. The processor, to work, does the same thing as an actual key-logger, but for the user and the OS instead of some illegal receiver. What do you think would happen if someone was able to add a small process in your PC so that the processor send all its data not only toward where it's supposed to go, but also to a third party?
As I wrote, the processor only uses raw data. This means that systems that shares data such as Cloud Services basically have this hole that allow anyone to access anything through the processor's real-short memory.
For something like a MMO, one example of use of this weakness in the hardware is that someone, through revert-engineering the data copied and send from the processor, could do anything on the data because he has a registry of everything that is going on in the cloud server.
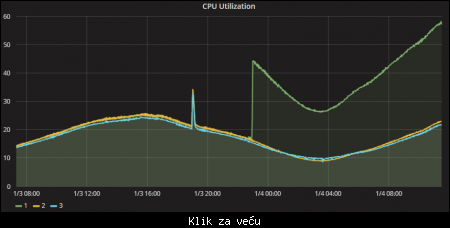
The fix that is currently being deployed is something really basic and explains why the CPU usage raise through the roof by as much as 40% if not more.
As I explained, the processor doesn't run encrypted data, but instead you got raw data that is encrypted by another processor's task after the raw data passed. The "fix" is to encrypt the data before passing the data (so the processor doesn't have a "log" of the raw file, but instead a log encryption.) This is because steps are not logged... only results of each threads.
Example is if you ask the processor to do a calculation like 10+100*(10/2)-5, it will returns 505. It will log the 505 for a really short while (still enough to be recorded), but it will not record the 10+100*(10/2)-5 steps.
But since the data is encrypted in the processor first, then you got to include the decryption "process" in the calculation process so that what was done with the raw data can be done with the encrypted data.
As the example, that's like if you ask the processor to encrypt something like a password : ABCDE and the encrypted result is 18437439205578, if then you request the processor to manage the task of confirming if it's really 18437439205578, you got to repeat, every time, the decryption process within the confirmation so that anyone who gets his hand on the data only reads 18437439205578 and not ABCDE.
It's 1 additional much more complex task in every steps that, originally, was simple as pie.
This is why the "fix" in the Cloud, in this case, double the CPU usage. as displayed in the graph.
The fix is basically:
Before: (RAW_DATA) > Processor > ENCRYPT_DATA > Processor > STORE_DATA > Processor, then when requested, DECRYPT_DATA > Processor > CHECK_DATA > Processor > ERASE_DATA > Processor.
Now (fix): (RAW_DATA + ENCRYPT_DATA) > Processor > STORE_ENCRYPTED_DATA > Processor, then when requested, (DECRYPT_DATA + CHECK_DATA) > Processor > ERASE_DATA_FROM_RAM > Processor.
With the fix, the processor isn't used as much, but each time, the calculated data is bigger.
(If you don't get why it's slower... It's similar to how we think when we calculate. What's faster?
(200+25) / 5
or
(A*20) + (B * 20 /10) where A is 0.5 and B is 17.5 which is confirmed in the CHECK_DATA request and is not logged.
While in both cases, the answer is 45, but before, someone who has access to the raw data and can reverse-engineer the data will immediately know it's 45 while the one who gets (A*20) + (B * 20 /10) won't know what to do with it because he/she lacks the A or B which is only "known" during the CHECK_DATA and not logged as it's part of the process request and not the results as CHECK_DATA returns a True or False (1 or 0) only.
[Link mogu videti samo ulogovani korisnici]
|