offline
- Sass Drake

- Anti Malware Fighter
Rank 2


- Pridružio: 26 Avg 2010
- Poruke: 10622
- Gde živiš: Hypnos Control Room, Tokyo Metropolitan Government Building
|
Napisano: 22 Mar 2012 20:25
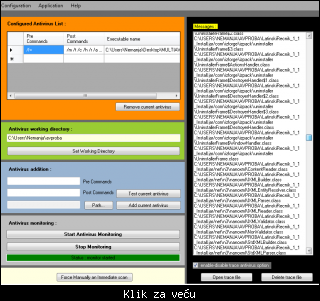
VirusBlokAda VBA32 CLI Scanner
DOWNLOAD
FREEWARE: NE*
* U VBA32Check paketu se uz VBA32 CLI Scanner nalazi i key fajl koji je potreban za potpuno funkcionisanje ovog skenera.
Način ažuriranja: Ručno pomoću batch programa koji je dio paketa. (update.bat)
Parametri:
VBA32{W|X}.EXE [path] ... [path] [/switch] ... [/switch],
where path - drive:\directory\...\directory\ or
*: - local drives, **: - network drives;
@filename - process files from filelist
SWITCH - specifies program options:
/?[+|-] - show help screen;
/H[+|-] - show help screen;
/HELP[+|-] - show help screen;
/M=1 - fast scanning mode;
/M=2 - optimal scanning mode (/AF+);
/M=3 - thorough scanning mode (/AF+ /PM+);
/AF[+|-] - all files;
/PM[+|-] - thorough scanning mode (VERY slow);
/RW[+|-] - detect Spyware, Adware, Riskware;
/CH[+|-] - switch on cache while scanning objects;
/FC[+|-] - cure infected files;
/FD[+|-] - delete infected files;
/FR[+|-] - rename infected files;
/FM+[directory]- move infected files to selected directory (by default C:\Virus);
/SD[+|-] - delete suspicious files;
/SR[+|-] - rename suspicious files;
/SM+[directory]- move suspicious files to selected directory (by default C:\Virus);
/BC[+|-] - cure boot sectors;
/NA[+|-] - disable detection for the signed file (only Windows);
/HA=[0|1|2|3] - heuristic analysis level (0 - disabled, 2 - maximum);
/MR=[0|1|2] - memory scanning (0 - disabled, 2 - full,
full is enabled by default);
/AS=[0|1|2] - scan files launched at system startup
(0 - disabled, 2 - full,
full is enabled by default, only Windows);
/BT[+|-] - boot sectors scanning (enabled by default);
/QI[+[directory]|-] - copy infected object to Quarantine;
/QS[+[directory]|-] - copy suspicious object to Quarantine;
/D=[N,][filename] - run program once in N days (by default 1);
/R=[filename] - save report to file (VBA32.RPT by default);
/R+[filename] - append report to file (VBA32.RPT by default);
/UL[+|-] - show report in UTF-8;
/L=[filename] - save list of infected files to file (VBA32.LST);
/L+[filename] - append list of infected files to file (VBA32.LST);
/QU[+|-] - allow the program to be interrupted (by default);
/DB=directory - search virus definitions update in
selected directory on startup;
/SS[+|-] - enable virus detection sound warning;
/OK[+|-] - include "clean" filenames in report;
/AR[+|-] - enable archives scanning;
/AL=[file_size,kB] - don't scan archives larger than the specified value;
/AD[+|-] - delete archives containing infected files;
/SFX[+|-] - detect installers of malware;
/ML[+|-] - mail scanning;
/MD[+|-] - delete messages containing infected files;
/VL[+|-] - view list of viruses known to program;
/VM[+|-] - show macros information in documents;
/SI[+|-] - additional information about program support;
/LNG=suffix - select language file VBA32<suffix>.LNG;
/KF={directory|path} - specify path to key file;
/EXT= - specify list of file extensions to be checked;
/EXT+ - add user defined file extensions to default list;
/EXT- - remove file extensions from default list;
/WK[+|-] - wait for any key when finished;
/SP[+|-] - show overall check progress;
/J[+|-|=thread_count] - multithreaded mode, count of simultaneously
processed files can be set to default value (-J, -J+,
preferred) or explicitely (-J=count);
The following switches are active by default: /QU /MR /BT /AS /RW
Dopuna: 05 Maj 2012 1:31
Dr.Web console scanner for Windows
DOWNLOAD
FREEWARE: NE
Način ažuriranja: Ručno pomoću drwebupw.exe koji je sastavni dio paketa
Parametri:
COMMAND LINE OPTIONS
To start the program, use the following command line:
<program> [disk:][path] [options]
where
program - executable module name (DrWebWCL);
disk: - logical drive of a hard disk, floppy drive, network drive, CD-ROM,
or * (all local logical drives);
path - location of files to be checked; it may contain path to the
directory on local/network drive (or network directory) and,
optionally, filename (or filename mask).
The command line may contain several [disk:][path] parameters delimited with
blanks. In this case, the program will sequentially scan the specified objects.
Command line options (delimited with blanks)
/@[+]<file> - check objects listed in <file>.
Each object must be identified on a separate line containing
a full pathname (to check file) or the "?boot" keyword (to check
boot sectors). The list file can be created with any text editor.
When scan is completed, Dr.Web deletes the list file, unless
"+" is included in the option;
/ADW[I|D|M|R] - determine the actions for detected adware: I - ignore;
D - delete, M - move (by default, to the INFECTED.!!! directory),
R - rename (by default, the extension's first character is changed to
"#");
/AL - scan all files on a given drive or directory;
/AR[D|M|R][N] - check all files inside archives (ARJ, CAB, GZIP, LZH, RAR,
TAR, ZIP...). Use the optional parameters to specify how archives with
infected (or suspicious) objects should be treated as a whole:
D - delete, M - move (by default, to the INFECTED.!!! directory),
R - rename (by default, the extension's first character is changed to
"#"); the N option suppresses the archive type after the name of the
archive file;
/CN[D|M|R][N] - determine how containers (HTML, RTF, PowerPoint,..) with
infected (or suspicious) objects should be treated as a whole:
D - delete, M - move (by default, to the INFECTED.!!! directory),
R - rename (by default, the extension's first character is changed to
"#"); the N option suppresses the container type after the name of the
container file;
/CU[D|M|R] - cure infected objects and delete incurable files. Or use the
optional parameters to specify how infected filed should be treated:
D - delete, M - move (by default, to the INFECTED.!!! directory),
R - rename (by default, the extension's first character is changed to
"#");
/DA - run Dr.Web only once in a day. For this option, the configuration file,
(INI-file) containing the date of the next scanning session must be
present;
/DLS[I|D|M|R] - determine the actions for detected dialers: I - ignore;
D - delete, M - move (by default, to the INFECTED.!!! directory),
R - rename (by default, the extension's first character is changed to
"#");
/EX - scan files that have extensions associated with executable modules
and MS Office documents (COM, EXE, SYS, BAT, CMD, DRV, BIN, DLL, OV?,
BOO, PRG, VXD, 386, SCR, FON, DO?, XL?, WIZ, RTF, CL*, HT*, VBS, JS*,
INF, A??, ZIP, R??, PP?, HLP, OBJ, LIB, MD?, INI, MBR, IMG, CSC, CPL,
MBP, SH, SHB, SHS, SHT*,MSG, CHM, XML, PRC, ASP, LSP, MSO, OBD, THE*,
EML, NWS, TBB);
/GO - run without asking you what to do next (in such situations as not
enough disk space for unpack operation, invalid parameters in the
command line, Dr.Web infected by unknown virus, etc.). This option
might be useful, say, for automatic check of incoming e-mail;
/HA - enable the heuristic analyzer that can detect unknown viruses;
/HCK[I|D|M|R] - determine the actions for detected hack tools: I - ignore;
D - delete, M - move (by default, to the INFECTED.!!! directory),
R - rename (by default, the extension's first character is changed to
"#");
/IC[D|M|R] - determine how to treat incurable files: D - delete, M - move
(by default, to the INFECTED.!!! directory), R - rename (by default,
the extension's first character is changed to "#");
/INI:<path> - use an alternative configuration file (INI-file);
/JOK[I|D|M|R] - determine the actions for detected joke programs: I - ignore;
D - delete, M - move (by default, to the INFECTED.!!! directory),
R - rename (by default, the extension's first character is changed to
"#");
/LNG[:<path>] - use an alternative language file (DWL-file), or built-in
(english) language;
/ML[D|M|R][N] - check files of mail format (UUENCODE, XXENCODE, BINHEX,
MIME,...). Use the optional parameters to specify how mail files with
infected (or suspicious) objects should be treated as a whole:
D - delete, M - move (by default, to the INFECTED.!!! directory),
R - rename (by default, the extension's first character is changed to
"#"); the N option suppresses the mail type after the name of the mail
file;
/MW[I|D|M|R] - determine the actions for all types of malware programs (i.e.
adware, dialers, hack tools, jokes, riskware): I - ignore; D - delete,
M - move (by default, to the INFECTED.!!! directory), R - rename (by
default, the extension's first character is changed to "#");
/NI - ignore the settings in the configuration file (DRWEB32.INI);
/NM - skip memory test;
/NS - run non-stop (no interruption by pressing ESC);
/OK - write a full list of scanned objects and display "OK" next to clean
objects;
/PF - display the "Scan another diskette?" prompt after checking a floppy
disk;
/PR - prompt to confirm an action on an infected or suspicious file;
/RP[+]<file> - write the scan results to a file (by default,
<program>.LOG), <file> is the full pathname of a report file. If the
plus sign is included, the recent report will be appended to the
report file; otherwise the report file will be overwritten;
/RSK[I|D|M|R] - determine the actions for detected riskware: I - ignore;
D - delete, M - move (by default, to the INFECTED.!!! directory),
R - rename (by default, the extension's first character is changed to
"#");
/SCP:<n> - specify the priority of the scanning process over other processes
in the system (n - number from 1 to 50; default value is 25);
/SD - scan subdirectories;
/SL - scan symlinks;
/SO - play sounds;
/SP[D|M|R] - determine how to treat suspicious files: D - delete, M - move
(by default, to the INFECTED.!!! directory), R - rename (by default,
the extension's first character is changed to "#");
/SS - save current settings when the program terminates;
/TB - scan boot sectors and master boot record;
/TM - scan memory for viruses (including Windows system memory);
/TS - scan startup files;
/UPN - disable the output of names of file packers used for packing the
scanned executable files to the log file;
/WA - wait after scan is finished if viruses or suspicious objects were found;
/? - display help.
If DBWEB32.INI is not present or not used, the default options are:
/AL /AR /HA /ML /PR /SD /SL /TB /TM /TS
Some options can be postfixed with the "-" character. This "negation" form
disables the respective function or mode. It might be useful if the mode is
enabled by default or via settings in the INI-file.
The negation form can be applied to the following command-line options:
/ADW /AR /CU /DLS /FN /HCK /JOK /HA /IC /ML /MW /OK /PF /PR /RSK /SD /SL /SO
/SP /TB /TM /TS /UP /WA
Note that the negation form of /CU, /IC and /SP cancels all actions enabled
by these options. It means that information about infected and suspicious
objects will appear in the report file only.
/AL, /EX and /FM cannot be used in the negation form. However, any of these
options disables the other two.
RETURN CODES
The values of the return code and corresponding events are as follows:
0 - OK, no virus found
1 - known virus detected
2 - modification of known virus detected
4 - suspicious object found
8 - known virus detected in archive (container, mail file)
16 - modification of known virus detected in archive (container, mail file)
32 - suspicious file found in archive (container, mail file)
64 - at least one infected object successfully cured
128 - at least one infected or suspicious file deleted/renamed/moved
|